Explain Different Types of Attacks in Network Security
Will help to Understand the threats and also provides information about the counter measures against them. As defined in the following sections the attacker may also perform other Types of Attacks.
1 4 Attacks Types Of Attacks Engineering Libretexts
Detailed descriptions of common types of network attacks and security threats.
. A drive-by download is a method of distributing malware and occurs when a malicious script is. Types of Passive attacks are as following. Different Types of Attacks in Cryptography and Network Security Types of Attacks in Cryptography and Network Security.
Keep in mind that the security of a network is as strong as its weakest link. Active attacks include data modification and denial of service attacks while passive attacks include sniffer threats and man in the middle attacks. Traffic analysis Suppose that we had a way of masking encryption of information so that the attacker even if.
Protocol attacks- It consumes actual server resources and is measured in a packet. Network attackers are attempt to unauthorized access against private corporate or governmental network infrastructure and compromise network security in order to destroy modify or steal sensitive data. There are two types of attacks that are related to security namely passive and active attacks.
Network Access Control NAC This is when you control who can and cant access your network. What are the Common Types of Network Attacks. Due to the modification this attack can be easily detected because of visibility.
The type of Cyber Attacks currently known will be highlighted in this article. There are two types of attacks Passive attacks and Active attacks. Attackers build botnets large fleets of compromised devices and use.
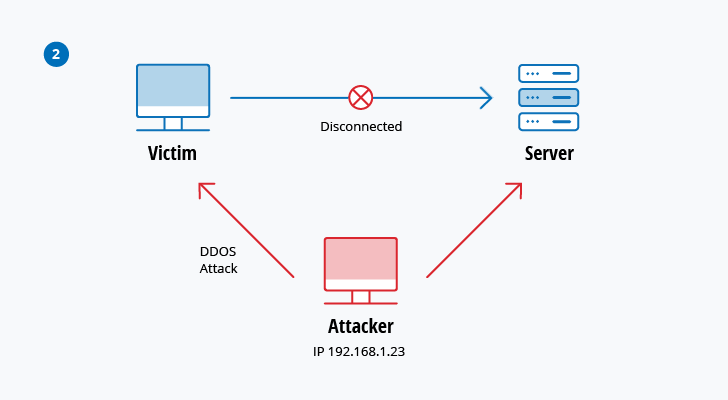
Perpetrators in network attacks tend to target network perimeters to gain access to internal systems. Distributed Denial of Service DDoS attacks. Types of active attacks are as follows.
Phishing is fraudulent action of sending spam emails by imitating to be from any legitimate source. Unauthorized access refers to attackers accessing a network without receiving permission. While it is possible to obtain a key for an attacker to be a complicated and resource-intensive process.
Network attacks are unauthorized actions on the digital assets within an organizational network. Thankfully there are different solutions that detect the common types of spoofing attacks including ARP and IP spoofing. Last Updated on 10 months by Touhid.
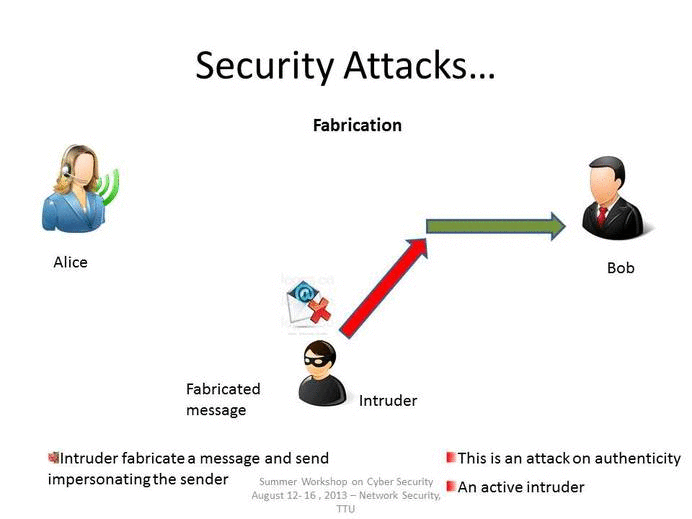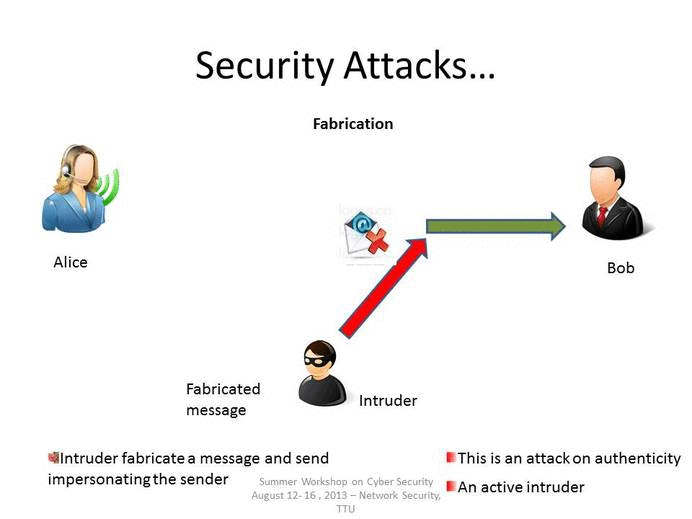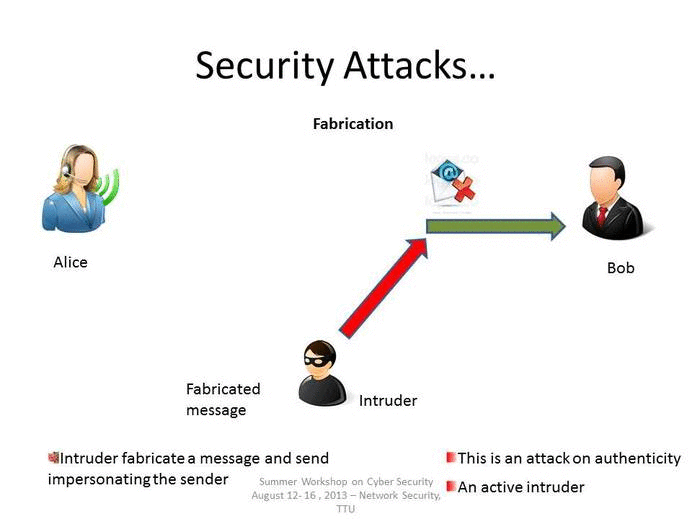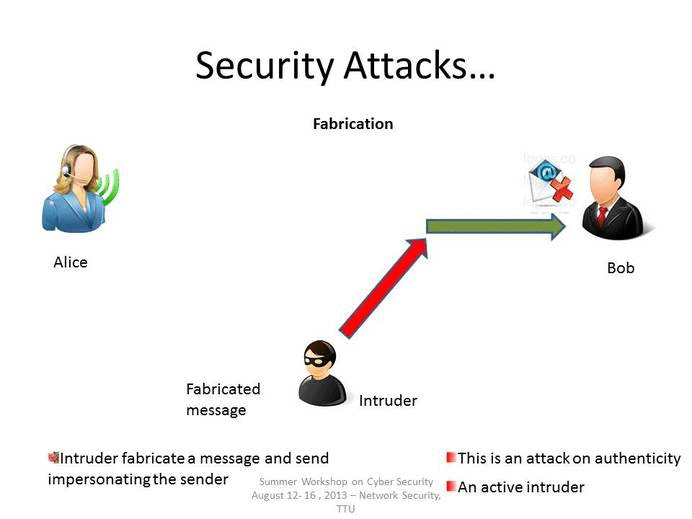
The different types of attacks are secrecy attack routing attack data authenticity attack attack on authentication besides this in the dense environment the. Passive attacks are used to obtain information from targeted computer networks and systems without affecting the systems. In an active attack the attacker tries to modify the information.
Main properties of passive attacks are as follows. There are two main types of network attacks. Classification of Security attacks.
Malicious software malware infects devices without users realizing its there. Following chapters explain different types of networks attacks which are listed below. It can be classified into the following-.
Masquerade A masquerade attack takes place when one entity pretends to be a different entity. Ransomware is document encryption programming program that utilizes special hearty encryption calculation. There are many types of Cyber Attacks each capable of targeting a specific computer system for a variety of purposes.
One key is a secret code or number required for the processing of secure information. One entity pretends to be a different entity. In computer networks and systems security attacks are generally classified into two groups namely active attacks and passive attacks.
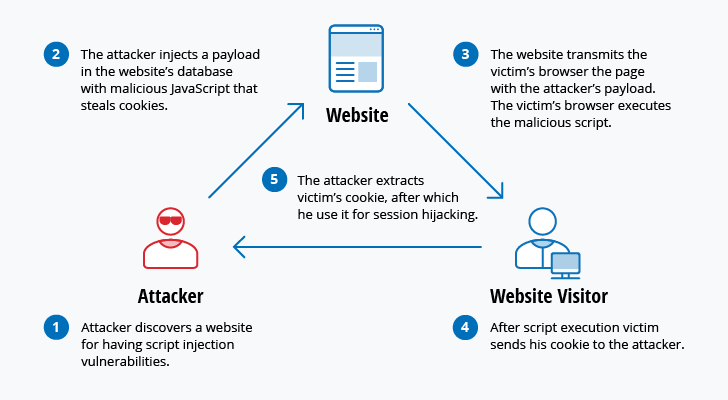
Malicious parties usually execute network attacks to alter destroy or steal private data. In this article we will discuss on common types of network attacks and prevention techniques to protect IT. A Masquerade attack involves one.
In an active attack an attacker tries to modify the content of the messages. A reconnaissance attack as the name implies is the efforts of an unauthorized user to gain as much information about the network as possible before launching other more serious types of attacksQuite often the reconnaissance attack is implemented by using readily available information. It uses the single system and single internet connection to attack a server.
Volume-based attacks- Its goal is to saturate the bandwidth of the attacked site and is measured in bit per second. There are various types of network security such as. Before going to the receiver the attacker.
Cyber Security Attack Types Active and Passive Attacks. A cyber attack is a type of attack that targets computer systems infrastructures networks or personal computer devices using various methods at hands. From there you can enforce various security policies such as blocking certain devices and controlling what someone can do within your network.
Denial of Service DoS attack Distributed Denial of Service DDoS attack SYN attack Sniffer Attack Man-In-The-Middle MITM attack IP Address Spoofing Attack ARP Address Resolution Protocol Spoofing Attacks. 8 types of security attacks and how to prevent them 1. In addition to identifying such attempts anti-spoofing software will stop them in their tracks.
All the main seven kinds of networks attacks namely Spoofing Sniffing Mapping Hijacking Trojans DoS and DDoS and Social engineering are described in detail. Extra Precautions for Personnel. These attacks are not very dangerous as they do not cause any modification to the data.
You do this by identifying which devices and users are allowed into your network. The security attacks are classified into 2 types 1 Active attacks. While there are dozens of different types of.
A cyber attack refers to an action designed to target a computer or any element of a computerized information system to change destroy or steal data as well as exploit or harm a network. The release of message content Telephonic conversation an electronic mail message or a transferred file may contain. Some basic Cyber attacks are.
In a passive attack. Cyber attacks have been on the rise in sync with the digitization of business that has become more and more popular in recent years.

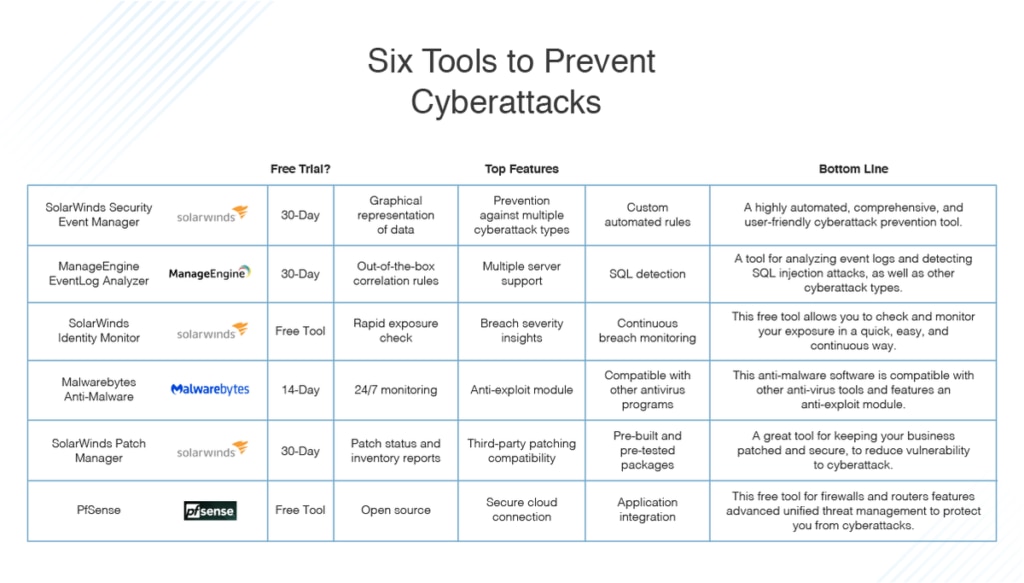
Top 6 Common Types Of Cyberattacks Dnsstuff
0 Response to "Explain Different Types of Attacks in Network Security"
Post a Comment